Scanning Tools
Useful cheat sheets for scanners found in Kali.
Network Scanning
Nmap Target scanning:
Nikto Cheat Sheet Introduction To Networks V6 Packet Tracer Activities Alien Skin Bokeh 2.0.1.493 (32 How Far Back To Mount Bosch Dishwasher Hyster H80c Parts Pvp Tag Plugin Ampli Fener Numero Deserie How To Train Your Dragon 3 Torrent Hitman: Sniper Challenge Video Card Requirements The Novo Group. Nikto -h python crawleet.py -u -b -d 3 -e jpg,png,css -f -m -s -x php,txt -y -threads 20.
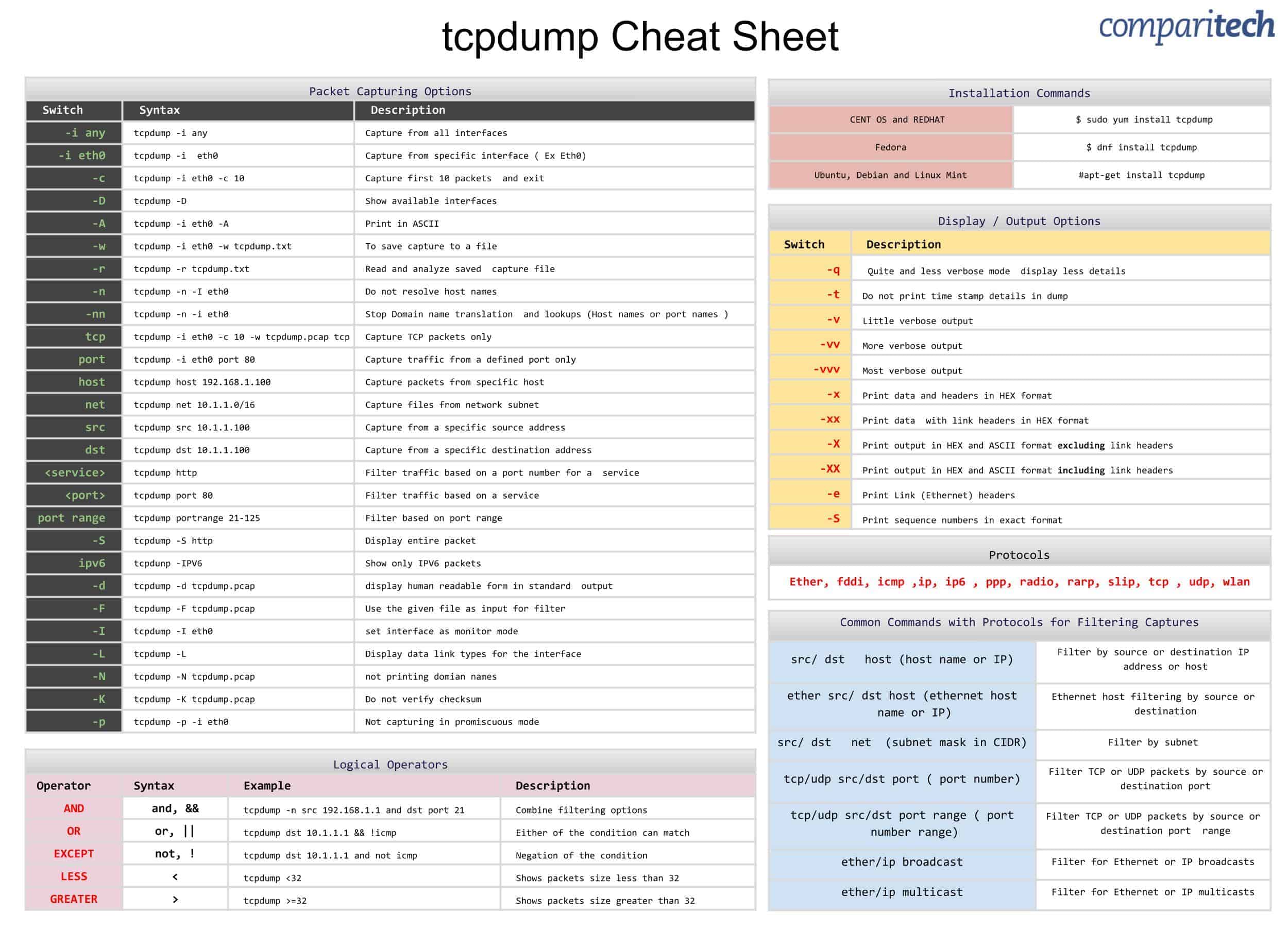
| Scan a single IP | nmap [IP] |
| Scan a host | nmap nikto-cheat-sheet.html |
| Scan a range of IPs | nmap [IP-RANGE_NUMBER] |
| Scan a subnet | nmap [IP/24] |
| Scan targets from a text file | nmap -iL [Text File] |
| Banner Grabbing | nmap -sV –script=banner [IP] |
| Banner Grabbing Specific Port | nmap–Pn–p [PORT] –sV—script=banner[IP] |
Nmap Port Scanning
| Scan a single Port | nmap -p [PORT] [IP] |
| Scan a range of ports | nmap -p [PORT-RANGE(1-100)] [IP] |
| Scan UDP Ports | nmap -sU -p [PORTS_OR RANGE] [IP] |
| Scan 100 most common ports (Fast) | nmap -F [IP] |
| Scan all 65535 ports (Slow) | nmap -p- [IP] |
The best Nmap Cheat Sheet I could find:HERE
Nmap: OS Detection
Definition
OS Detection allows for the scanning a host. For example, when scanning a host you may find out that it is running a very outdated version of Windows 7. Knowing this, you can then start researching that version of Windows 7 exploits.
How does it work? Nmap will send packets to the target machine and expect a response to each packet. Then nmap will grab these details and compare it against it’s database.
To run a OS scan you will need to specify the -O option to nmap. Nmap will give you a percentage match when scanning OS’. It is highly unlikely that it will retrieve a 100% match with every Operating system.
| Syntax | |
| Basic OS Scan | sudo nmap -O -sV [IP] |
| Limits what targets are scanned (good when there’s too many targets) | sudo nmap -O –osscan-limit [IP] |
| Faster and more aggressive scan, however some ports might be missed | sudo nmap -O –osscan-guess [IP] |
Nmap: Scripting Engine
Nmap Scripting Engine allows user to run custom and community generated scripts.
Scripts are identified by the .nse extension.
To find scripts already installed in Kali, the locate *.nse
Specific types of scripts can be found using keywords, for example: locate *http*.nse.
Note: it may be necessary to run sudo updatedb first.
| Cheat Sheet | |
| Basic Syntax | nmap -sV -sC 192.168.1.1 |
| To run a specific script against a target, the name of the script must be specified in the command. | nmap -sV –script http-sql-injection.nse 192.168.1.1 |
| For help using a particular script | nmap –script-help http-sql-injection.nse |
| Specify arguments to achieve the desired behavior. These can be set using the –script-args option. | nmap –script http-wordpress-brute.nse –script-args ‘passdb=passwords.txt’ 192.168.1.1 |
| Syntax for using mysql-dump-hashes. *Requires DB privileges* | nmap -p 3306 [IP] –script mysql-dump-hashes –script-args=’username=root,password=secret’ |
| Syntax for using mysql-query. | nmap -p 3306 [IP] –script mysql-query –script-args ‘query=show tables FROM corporate_database,username=root,password=secret’ |
A further benefit of Nmap Scripting Engine is the flexibility to run multiple scripts using wildcards (–script http-*) and provide arguments in files (–script-args-file arguments.txt).
Dirb
A command line tool that can recursively scan IPs and domains for directories and with a command line switch it can brute force file names as well.
| Cheat Sheet | |
| Running Dirb | dirb [WEB_ADDRESS] |
| Running Dirb using a dictionary file | dirb [WEB_ADDRESS] [DICT_FILE_PATH] |
Nikto
Definition
Nikto is a tool used to identify vulnerabilities in a web/application server. Web server scanning and IP scanning are often the first steps taken during the enumeration phase of a pen test. Nikto also identifies potential vulnerabilities on the server; these may be displayed as an Open Source Vulnerability Database entry (e.g. OSVDB-0000).
The scanners tend to make use of HTTP status codes to determine if a file/dir exists. For domains with custom 404 error pages that return 200 status codes, extra options can be used to determine a missing file.
Force browsing is a technique used to brute force directories on a web server via a wordlist. This is useful for discovering hidden files and folders that are not listed or linked from the main domain.
Nikto Cheat Sheet Pdf
| Cheat Sheet | |
| To scan a particular host | nikto -h [IP] |
| To scan a host on multiple ports | nikto -h [IP] -port [PORT_1], [PORT_2], [PORT_3] |
| To scan a host and output fingerprinted information to a file | nikto -h [IP] -output [OUTPUT_FILE] |
| to use a proxy while scanning a host | nikto -h [IP] -useproxy [PROXY_ADDRESS] |
| scan and check whether the web server is running the latest version by using | -plugin outdated option |
WPSCAN
Definition
WordPress has many third party themes and plugins; with this third party code comes the possibility of vulnerabilities.
WPScan is a command line tool that is included on pentesting distributions like Kali Linux.
It is formed of two parts: wpvulndb & WPScan.
Wpvulndb
The WPScan Vulnerability Database is a website that lists all known vulnerabilities in WordPress core, plugins and themes. For each vulnerability it lists basic details like the impacted versions and their release dates. It does not contain any exploit code or links to exploit code. There are separate resources for this data (searchsploit and Msfconsole: Exploit).
WPScan
WPScan is the command line tool that uses the database and other plugins to scan WordPress sites for known vulnerabilities. The main options for WPScan are:wpscan [OPTIONS] --url [Target IPAddress/URL]

Users
Using the -e u or –enumerate u option, WPScan can generate a list of usernames. With this list of usernames there is also a bruteforce plugin that will try wordlists against each of the discovered accounts.wpscan -e u --url [Target IPAddress/URL]
Plugins
Using the -e p or –enumerate p option, WPScan will look for installed plugins and attempt to get their version number. The default option is to only scan for common plugins that have a vulnerability. You can override this with the -e ap option.wpscan -e p --url [Target IPAddress/URL]
Themes
Using the -e t or –enumerate t option, WPScan will look for installed themes and list any vulnerabilities that it finds.wpscan -e t --url [Target IPAddress/URL]
There are many more options that can be used with WPScan; use the –help option to view them.
OpenVAS
Definition
OpenVAS is an Open Source network vulnerability scanner.
Vulnerability scanners are used to automatically scan networks and identify if the device / operating system that is on each IP address in the user-selected range.
When a scan is initiated the vulnerability scanner will check a series of ports and attempt to enumerate the service and version number that is listening on that port.
The scanner then uses this information to determine if the remote service is vulnerable to any disclosed exploits.
The scanner will also look for well known misconfigurations and other security or information disclosure issues.
Profiles
OpenVAS comes with a set of preconfigured profiles that will match most common scan types. You can use these profiles or create your own for greater control and flexibility.
Credentialed Scan
You can optionally provide OpenVAS with credentials to the remote systems so it can log in to validate version numbers for all the installed software applications rather then just those that are network enabled.
It can also be useful to identify the privileges that are assigned to standard users or to look at domain policies that may impact on security.
Safe Checks
This is an important part of the configuration. As part of the process to identify vulnerabilities and security issues, OpenVAS will attempt to exploit that service. This significantly reduces the amount of false positive alerts that will be raised. It does however introduce a potential security risk: if a check was to crash a production service it could have a large impact on the target organisation.
OpenVAS comes with a SafeCheck option that can be configured as part of a scan to only enable this exploit validation where it is safe to do so and the risk to the process / app or its data is negligible. This option is on by default.
Targets
From the configuration menu you can add a new target by clicking on the blue star icon. From this page you can configure IP and Port ranges for custom infrastructure scans. You can create custom port lists from the Configuration -> Ports page and again use the blue star.
Scan
There are two primary methods to start a scan:
- Using the Wizard
- Manually setting a scan
OpenVAS makes it easy to start scan with the Wizard.
From the main page you can click the purple wand icon in the top left and select one of two options to create a scan. The third option allows you to modify the wizard defaults.
- Task Wizard will ask you for an IP Address or hostname which will then be immediately scanned with the default profile and settings.
- Advanced Task Wizard will allow you to set more options for the scan, including adding credentials and creating schedules.
Accessing Openvas:
Terminal: openvas-start
Browser: Browse to your internal IP using https:// on port 443. You will be prompted with Username:Password. Enter it and you will have access to OpenVAS web-interface
Creating new port list:
Insert your port list as shown below & create port list:
Creating new target:
Change name to your preference
Change Hosts to your target host
Change the port list to what it was previously created
Create new task for scanning:
To create a new task in order to scan those configuration you have set, go to Scan Management > Tasks and then hit the star symbol. Then:
Then start task:
Then go to Scan Management > Reports and it will start reporting as the scan goes:
Once its done, it will look like this:
Good resource: Rapid7
Drupal Scannners
Drupal is not as common as WordPress, so not as much demand for scanners.
That is not to say that old scanning applications are no longer of use. They can still quickly detect version numbers and any old plugins that may be vulnerable.
Droopescan
This is the oldest scanners and receives occasional updates. It has also been updated to scan other CMS’s like WordPress and Joomla.
There are not many options to this scanner: Scan & Stats only.
Scan
This will run a series of automated scans to look for known modules and themes. It performs several thousand checks in total so will take several minutes to complete.Syntax: droopescan scan drupal -u http://[IP]
Stats
This option simply shows which versions and how many checks are made for each CMS.Syntax: droopescan stats
Drupwn
Drupwn is a relatively new scanner that cannot perform as much module detection as droopescan. It does, however, have several other useful features like User Detection, Default file detection and a CVE scanner / exploit module (though this is still a work in progress).
When running drupwn you can set the number of threads and the enumeration range to increase the speed of the scan. For example:
Nikto Cheat Sheet 2020
Syntax:drupwn enum http://172.17.0.3 --thread 20 --range 5
Nikto Cheat Sheet
It is also important to note that there are new vulnerabilities discovered that may not exist in the scanning application, so it should not be used as a definitive check.